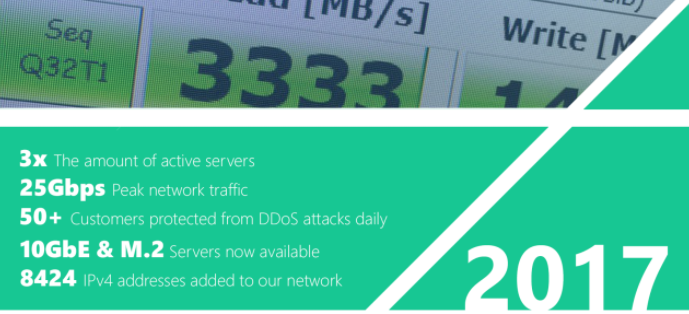
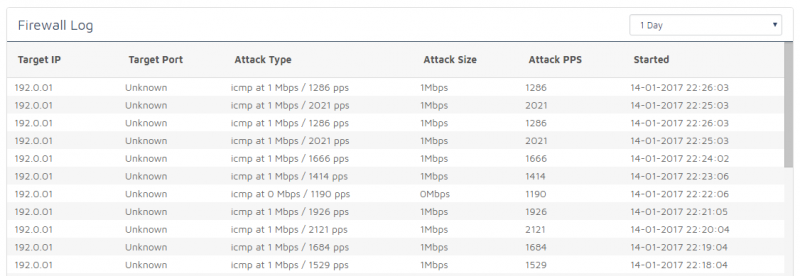
After months of testing and hundreds of packet captures, our new Corero SmartWall solution is now live network wide in both our London and Bristol locations.
Why Corero?
During our testing phase, we tried many different DDoS mitigation appliances and Corero came out on top each time. Here is what we looked for during the process.
- Raw filtering capacity — Corero provides line-speed filtering with 20Gbps of capacity per SmartWall block, allowing 80Gbps in just a 1U space through their modular design.
- Inspection techniques — We found many DDoS appliances could not detect the sort of attack patterns that we face daily without deep packet inspection. Corero provides a layer by layer filtering system at almost line rate speeds and thus allowing us to detect and mitigate even the smallest of attacks very easily.
- Support & Management — This is where Corero really shined and ultimately a huge factor in us choosing their product. Their support from day one was excellent in terms of response times, knowledge and going out of their way to make sure we were 100% happy.
Why the switch?
The reason for switching to our own in house mitigation platform came about after experiencing problems with mitigation / network performance whilst using Voxility previously.
Using Corero puts us in the driving seat and allows us to work on new custom filters for customers in short timeframes, and also allows us to work alongside a company that’s business is providing network security solutions day in, day out to further safeguard our own customers against new and emerging threats.
Why is this solution any better than before?
Previously when using Voxility for DDoS protection we were governed by their off ramp mitigation method, which involved a flow sensor monitoring their network for potential attack traffic patterns, then in the event one was detected it would inject a /32 route for the target of the attack into the network to redirect the traffic to the closest filtering unit. After this was done the filter would then tunnel the “clean” traffic downstream to a switch / router as close to the end destination as possible. This would take potentially up to 15-20 seconds to happen during an attack, depending on the size. Or not at all with smaller UDP floods, specifically targeting game, or voice servers. This is where our new solution excels!
With our new Corero protection solution deployed in line within our network it offers the fastest possible time to mitigate attack traffic, because the attack traffic enters the Smartwall TDS unit first before the rest of the network. There is no need for off-ramp traffic re-direction, or prefix prepending meaning no latency increases whatsoever! Just a smooth steady flow of clean traffic direct to your server.
zare.com/dedicated-servers