SLA Information – November 9 incident Roubaix (RBX)
On Thursday November 9, some of your services were affected by a network incident in our French site, in Roubaix (RBX). We would like to extend our sincerest apologies.
Flagged at 8:01am (French time), the incident was declared closed by our teams at 10:34am (French time). You were unable to access your services during this time.
All of your services are now working again, and we are here to answer any questions which you may have regarding your products.
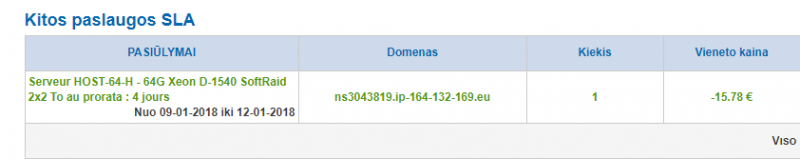
We are well aware of the consequences of this service interruption, and we will, of course, be activating the planned compensation for products which are contractually bound by an SLA. As a reminder, you can find all the SLA levels pertaining to your products, in the customer control panel. You can view all compensation details via this link.
тут-адрес-панели/billing/sla/
The causes of this incident are still being analyzed, and we have already taken some measures which will further strengthen the reliability of our services, even in the most unexpected situations.
You can find additional information about the event and the resulting actions here. Rest assured that we are doing everything to learn from each new situation encountered, to further improve our service availability. We will keep you informed of the implementation of these measures.
We are very sorry for the inconvenience this incident may have caused, and would like to reiterate our sincerest apologies.
Regards, The OVH team
от редакции
по русски написано ТУТ
Flagged at 8:01am (French time), the incident was declared closed by our teams at 10:34am (French time). You were unable to access your services during this time.
All of your services are now working again, and we are here to answer any questions which you may have regarding your products.
We are well aware of the consequences of this service interruption, and we will, of course, be activating the planned compensation for products which are contractually bound by an SLA. As a reminder, you can find all the SLA levels pertaining to your products, in the customer control panel. You can view all compensation details via this link.
тут-адрес-панели/billing/sla/
The causes of this incident are still being analyzed, and we have already taken some measures which will further strengthen the reliability of our services, even in the most unexpected situations.
You can find additional information about the event and the resulting actions here. Rest assured that we are doing everything to learn from each new situation encountered, to further improve our service availability. We will keep you informed of the implementation of these measures.
We are very sorry for the inconvenience this incident may have caused, and would like to reiterate our sincerest apologies.
Regards, The OVH team
от редакции
по русски написано ТУТ